This post is going to be a rather strange post compared to previous ones. But bear with me, in the middle of the post you will see why this post fits the IT security topic.
I'm also terribly sorry for not posting recently, but I was busy with my
SPSE and
SLAE certification. Both are recommended for Python and Assembly noobs like me. But back to this post.
A little bit of history
Cheating in games started as help for game testers. By using invincibility or infinite ammo testers were able to test the game quicker, which meant less money spent on testing. I personally use cheat codes in games, depending on my mood. Sometimes it feels good to slash all the opponents while I'm invincible, sometimes it is more fun to play the game without cheats. One can argue whether cheating in games is OK or not, but I believe it depends, there is no black or white. But one thing is for sure, it is part of the gaming industry. There is huge demand for cheats. There were even cheat books printed on paper...
The different types of cheats (on PC)
There are different types of cheats in PC gaming. Following is a noncomplete list of these cheats:
Cheat codes
The good old IDDQD type of cheats. These are left in the game by the developers intentionally. Nothing interesting here.
Edit memory
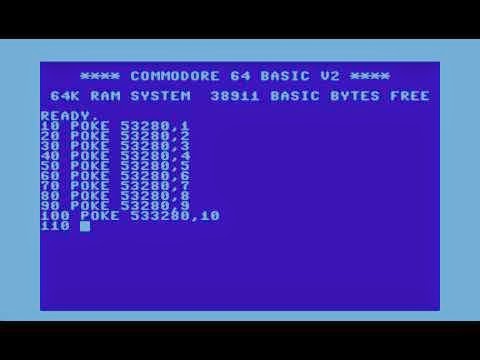
This is my favorite. I will talk about this at the end of the post. Whenever a user launches a new program, the program's whole memory is accessible (read/write) to every other program launched by the user. And since the memory stores the current game state (health, ammo, armor, etc.), these values can be changed easily. In the good old times, there were
POKE commands to do this cheats, and the memory address to write into was published by people who found where the game stores the most critical states about the game.
Code injection
This is like patching the game code. For example, one can change the "DEC (pointer to your current health)" instruction with NOP (do nothing), thus becoming invincible. In multi-player cheats, there is the aimbot to help you aim at enemies, wallhack to see through the wall, increase hitbox of the enemy for smoother hit, or in MMORPGs, one can write macros to collect items while the player is not online. I would say the so-called "
trainers" more or less fit into this category and the previous one.
Saved game editor
The first time a kid meets a hex-editor (just like the co-author of this blog did with SIM City when he was 10 years old - David). It can teach a lot about file structures, the hexadecimal numeral system, etc. Fun times.
Hacking game server
Not very common, but even more fun. Warning: endless trolling possibilities in multi-player games ahead :) How to hack a game server? Well, I think this might deserve another full blog post ...
Network traffic hacking
One last necessary type of cheating is to modify network traffic between the client and the game server. AFAIK SSL is not universal in gaming, so stunnel is not needed for this hack, but ettercap can help in changing the communication.
Why cheating becomes more critical (and challenging)?
Now in the age of in-app-payments, the game creators are no longer thinking about cheats as funny things but something to be destroyed to the ground. Because cheating decreases its revenue. Or not. At least they think it does. To quote Wikipedia here, "cheating in such games is nonetheless a legal grey area because there are no laws against modifying software which is already owned, as detailed in the Digital Millennium Copyright Act."
A lot of online games include anti-cheating components like PunkBuster, nProtect GameGuard, or Valve Anti-Cheat. This whole cheating/anti-cheating industry is the same as the virus/anti-virus industry. A cat and mouse game.
Freemium games
If you have not played with "freemium" games, you should watch South Park season 18, episode 6. - "Freemium Isn't Free." If you did play with freemium games, you definitely have to watch it :) There are many problems with freemium games. It is free to install, free to play. The first 3-4 hours might be fun to play. But after that, it turns out it is impossible to advance in the game without paying money for it. And by spending cash, I mean spending a LOT! Let's have a look at today's example, an arcade racing video game.

For 99.99 USD, you can get 3 000 000 credit. For almost double the price of a new PC game, you can get these credits. In this particular game, I estimate one have to play ~6-24 hours constantly to get this amount of credit. But by playing ~6 hours, I mean 6 hours without progress in the game! Kind of boring. And what do you get from 3 000 000 credit? You can buy one of the most expensive cars, but can't tune them fully. You have to play more (without progress) or buy more. But guess what, there are more cars you can't buy by only playing the game. Those are only available via in-app-purchase.
Even though the player has 58 765 533 credits, it is not possible to buy this car. Only available through real money.
So, what are your possibilities? You are either Richie Rich, and can afford the money to buy these. Or you can be insane, and try to play the game without in-app-purchase. Or give up the game and try another freemium ... Or, you can try to hack the game!
Hack all the freemium games!
Although I was not playing this racing game from day one, I was able to witness the evolution of the cheats against this game. The cheats which worked in one day was not working one month later. The game is continuously updated to defeat the newly published cheats.
Noob start
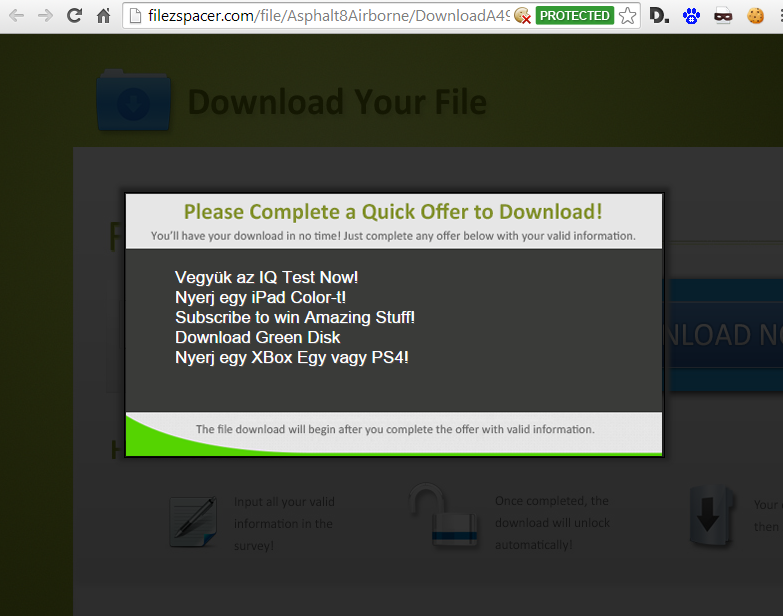
So, I want to hack this game, what is the first thing a noob like me does? Bing it! Google it!
From the first page result, let's check this tool:
While trying to download that, I just have to give my email address to spammers, or my mobile number will be subscribed to premium rate text messages. What fun.
Another "cheat" program will install malware/adware on your computer. Never ever try these programs. They are fake 99% of the time and after installing those you will have another problem, not just how to hack freemium games.
Beginners start - Cheat engine
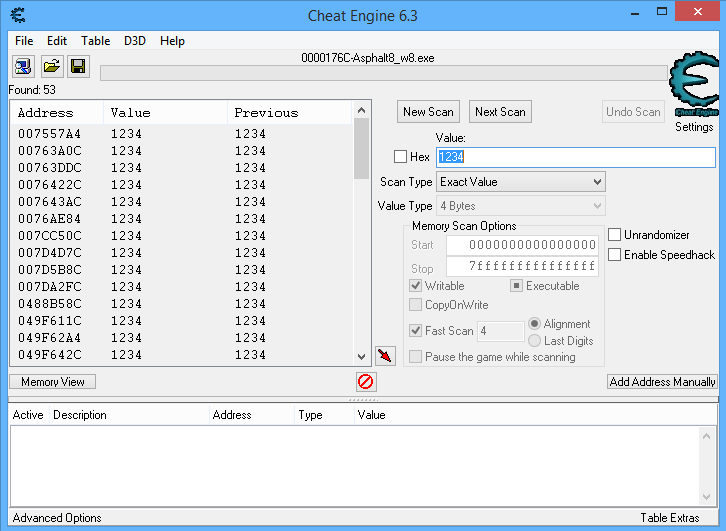
When I first heard about hacking games in memory, I visualized hours of OllyDBG/ImmunityDBG/(insert your favorite Windows debugger here). It turned out, there are some specialized tools to help you with cheating the game. No assembly knowledge required. My favourite tool is CheatEngine. I highly recommend to download it and spend 10 minutes to get past the built-in tutorial levels to get a feeling about this tool. It's super duper awesome.
When I first tried to hack this game myself, I scanned the memory for my actual credit and tried to change that, no luck. Keep reading, you will see what happened.
The second cheat I tried with cheat engine was
something like this:
- Start the game, play the first level, and check how many credits is paid for winning the race. Pro tip: use dual display for full-screen game cheating.
- Restart the same level, attach Cheat Engine to the game's process
- Scan the memory for the same value at the beginning of the race
- Scan the memory for the same value at the end of the game. The intersect of the first and second scan includes the real value where the credit is stored for winning the race.
- Change the values (both the real one and some false positives) to something big
- Watch the game to crash
- Be amazed at the money you received
Nowadays, most of the cheats on YouTube does not work. Except for these
kind of cheats. I don't want to recreate that tutorial, so you should watch it first then come back.
Are you back? Great. Do you have any idea what have you just seen? No? Well, in this case, don't try this at home. Copy-pasting
assembly code from random internet posts and running on your computer is always a bad idea. It is precisely as risky as downloading free programs from random internet sites.
Although I have not seen people trolling others with this cheat engine type of shellcode, I think the time will come when these will be turned into something terrible. These shellcodes might work, or might harm your computer. The good news is, we can have a look at the code and analyze it.
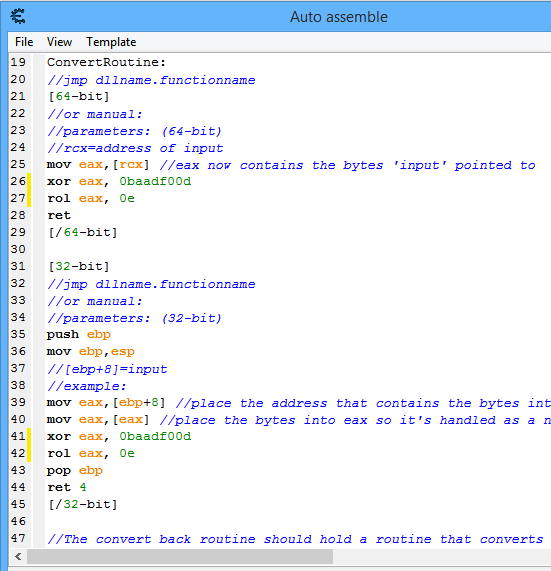
When you open CheatEngine and try to define a new custom type, you are greeted with a skeleton assembly code. I don't want to detail what all the skeleton code does, let's just focus on the difference between the skeleton code and the code used in the video. This is the "decrypt function":
xor eax, 0baadf00d rol eax, 0e
What does it mean? The actual credit is encrypted in memory. If you want to scan it in memory, you won't be able to find it. But! The encryption is rotating the value to the right (ROR) with 0xE (14 in decimal), and after that, it is XOR-ed with 0xbaadf00d. Decrypting it is the inverse of the functions in reverse order (in this particular case, the order does not matter, but that's not the point). The inverse function of XOR is XOR, and the inverse function of ROR (rotate right) is ROL (rotate left). Now that we analyzed the assembly code, we can be sure that it is safe to execute. Just follow the video and see your coins falling from the sky. For free. In a freemium game. Have fun!
Encrypt memory - applications at financial institutions
Another exciting thing is that I don't recall any thick client applications in the financial industry encrypting the values in memory. And I agree, there are more significant problems with thick client applications than not encrypting the essential values in memory. But still, some thick client applications are regularly updated, maintained. Maybe it is a good idea to encrypt the values in memory. It will make attackers' life harder. Not impossible, but harder. Perhaps the developers of these applications should learn from the gaming industry (or from malware developers for that matter) because it is a shame that an arcade racing game or an FPS is protected better than an application responsible for transacting millions of dollars. Just think about the RAM scraping malware stealing millions of credit card data ...
Moral of the story
Cheating is part of the gaming history, and the freemium games are trying to take away the cheats from the gamers because they want money. Thanks to CheatEngine and some clever hacks, these programs can be still beaten. And guess what, there is CheatEngine for Android - although it did not work for me on the latest Android. And sometimes, hacking all kinds of applications can be more comfortable with CheatEngine, compared to traditional debuggers.
Also, always check the code before executing it! And when you find something cool, publish it, so everyone could enjoy the games!
More information- Hack Tools Online
- Hacker Tools 2020
- How To Install Pentest Tools In Ubuntu
- Hacking Tools For Games
- Hacker Security Tools
- Hacker Tools For Pc
- Hacking Tools 2019
- Pentest Tools Website Vulnerability
- Hacker Tool Kit
- Hacking Tools Free Download
- Underground Hacker Sites
- How To Make Hacking Tools
- Termux Hacking Tools 2019
- Hack Tools
- Best Hacking Tools 2019
- Hack Tools
- Pentest Tools Kali Linux
- Hack Tools For Games
- Top Pentest Tools
- Physical Pentest Tools
- Pentest Tools Nmap
- Hack Tool Apk No Root
- Hack Tools For Windows
- Nsa Hack Tools Download
- Black Hat Hacker Tools
- Hacker Security Tools
- Pentest Reporting Tools
- Hacker Tools For Windows
- Hack Tools For Ubuntu
- Hack Tools 2019
- Hacker Tools Github
- Hacking Tools Free Download
- Pentest Tools For Windows
- Pentest Tools Github
- Nsa Hack Tools Download
- New Hack Tools
- How To Make Hacking Tools
- Best Hacking Tools 2019
- Hacker Tools For Ios
- Hacker Tools Windows
- Hacker Tools For Windows
- Nsa Hacker Tools
- Pentest Tools Tcp Port Scanner
- Top Pentest Tools
- Pentest Tools Website Vulnerability
- Hacking Tools Software
- Hacking Apps
- Pentest Tools Website
- Pentest Tools For Android
- Pentest Tools Review
- Hacker Tools Online
- Hacking Tools For Windows 7
- Hacker
- Pentest Tools Alternative
- Hacking Tools Windows 10
- Hack Tools
- Hacking Tools Download
- Hack Tools For Games
- How To Make Hacking Tools
- Pentest Reporting Tools
- Hacking Tools 2019
- Nsa Hack Tools Download
- Hacker Tools Github
- Tools Used For Hacking
- Underground Hacker Sites
- Hacking Apps
- Hack Tools Pc
- Pentest Tools Linux
- Pentest Tools Url Fuzzer
- Hacking Tools For Windows Free Download
- Game Hacking
- Pentest Tools Website
- Hacker Tools Software
- Hackers Toolbox
- Hack Tools For Pc
- Hacker Tools For Windows
- Hacking Tools
- Hacking Tools Software
- Hacking Tools For Games
- Hacker Tools For Mac
- Tools For Hacker
- Hack Tools For Games
- Hacker Tools For Windows
- Hack Tools For Windows
- Hacking Tools For Beginners
- Hacking Apps
- Hacker Tools
- Hack Tools
- Hacking Tools Online
- Hacker Tools Free Download
- Pentest Tools Tcp Port Scanner